A Pentagon of Considerations Towards More Secure Blockchains
Qi Zhang, IBM Thomas J. Watson Research, Yorktown Heights, NY, USA; Reza M. Parizi, Department of Software Engineering and Game Development, Kennesaw State University, GA, USA; and Kim Kwang Raymond Choo, Department of Information Systems and Cyber Security, University of Texas at San Antonio, Texas, USA
IEEE Blockchain Technical Briefs, September 2018
With the rapid growing interest in cryptocurrencies such as Bitcoin and Ethereum, their underlying technology, blockchain, is catching huge amount of attentions from both academia and industries. More than a distributed database, blockchain is able to establish trust among multiple untrusted participants. This is achieved by using cryptographic techniques such as hash pointer [4], and consensus algorithms such as Proof of Work (PoW) [5].
As a trusted platform, blockchain finds itself a good fit in many use cases, especially when multiple untrusted participants need to be involved. For example, Walmart is collaborating with IBM to use the blockchain (Hyperledger Fabric) to enable the safety, transparency, and efficiency of their food supply chain, in which the farmers, distributors, wholesalers, and etc. are involved. Also, many financial institutes are sitting together to actively explore using blockchain to facilitate the process of onboarding customers and to build faster inter-bank payment systems. In these cases, the use of the blockchain reduces the cost of having a third party to validate all the transactions, improves the traceability and auditability of the recorded data, thus makes the whole process more efficient.
Although the blockchain platform is described as tamper-proof, it is not impossible to be tampered with. The security of the platform and the privacy of the data stored in the blockchain ledger are still the top concerns of the practitioners. Therefore, it is extremely important to understand how reliable the existing blockchain technology is and what are the efforts to make it more secure and provide better data privacy.
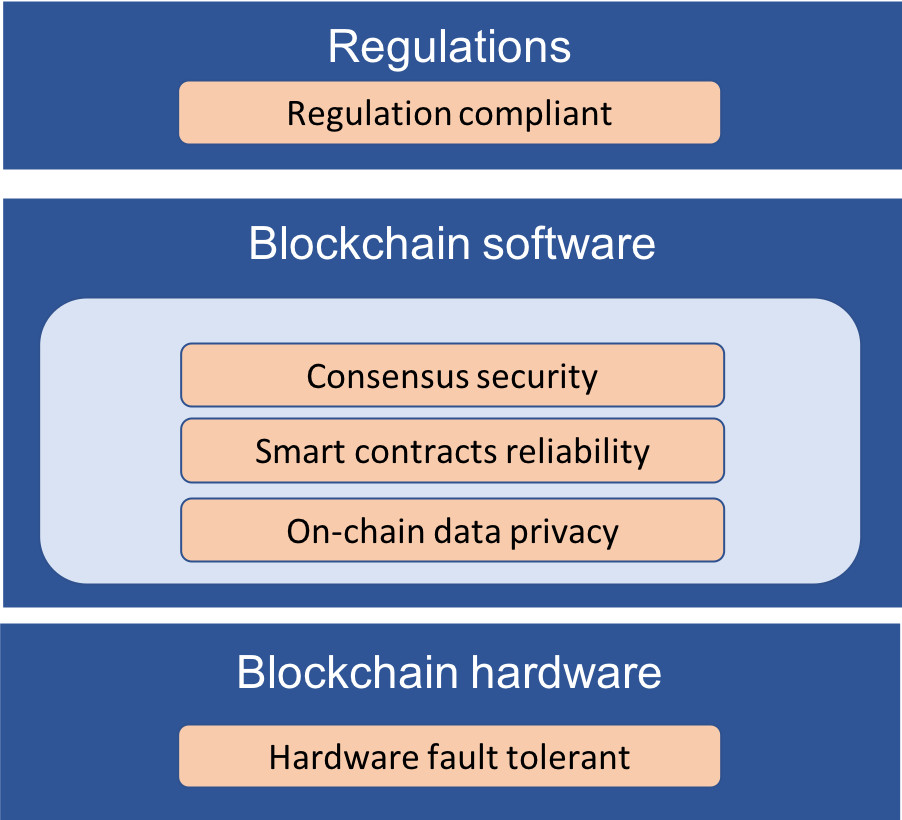
Figure 1. Blockchain Security Considerations.
This paper investigates five critical factors that need to be considered towards building more secure blockchains – consensus security, smart contracts reliability, on-chain data privacy, hardware fault tolerant, and regulation compliant. As shown in Figure 1, these factors spam across the blockchain hardware, software, as well as its related regulations. For each factor, this paper discusses its importance and explores both the state-of-the-art solutions and the future opportunities.
Consensus security
Blockchain platforms rely on the consensus algorithms to ensure that it is extremely difficult for some malicious users to subvert the whole network. As an example, Proof of Work is one of the consensus algorithms that is Byzantine fault tolerant, in which miners compete with each other to publish blocks via solving a cryptographic puzzle. In order to successfully commit a malicious transaction (e.g. a double spend transaction) into the ledger, an attacker needs to have more than half of the whole computing power of the network. This supposed to be almost impossible given the large number of the participants in the network. However, with the appearance of powerful mining pools, the blockchain could be subverted if multiple large mining pools decide to join and hack the network together. Other than Proof of Work, many other consensus algorithms, such as Proof of Stake [11] and Proof of Elapsed Time [12], are also proposed. Some analysis has been made regarding to the security of different consensus algorithms [2]. The better we understand their vulnerabilities, the more secure the blockchain platform can achieve.
Smart contracts reliability
Smart contract is the key of blockchain-based applications, turning the blockchain into a decentralized computing platform. It executes the logic of the transactions on the blockchain and the results of the successfully executed smart contracts are recorded in the blockchain ledger. Even with a secure consensus algorithm, the vulnerability of the smart contract is also detrimental. Due to a bug in the smart contract, the famous DAO hack [6] managed to steal more than $60 million worth of ether by carrying out a reentrancy attack [7]. Such attacks have raised developers’ awareness of creating highly secure smart contract. Given the smart contracts can be written in many different languages, such as Solidity in Ethereum, Go and Java in Hyperledger Fabric, exploring the vulnerabilities of such programming languages and understanding how to prevent them in a blockchain environment is very necessary. For the developers, it is essential to thoroughly validate the security of their smart contracts before deploying them on the blockchain.
On-chain data privacy
In blockchain, transaction data are shared by all the participants, this could be problematic for data privacy, especially if some of these transactions are confidential. This could also be a significant obstacle for blockchain to be widely accepted. Efforts have been made to preserve the on-chain data privacy. For cryptocurrency blockchains, instead of having real user name or ID in each transaction, a user on a blockchain is represented by a key, which is a string of characters that has nothing to do with the user’s real-world identity. Also, a user on the blockchain can be represented by multiple keys instead of one, which further reduces the probability of identifying a user by such keys. However, anonymizing the user ID is not entirely privacy-preserving. Given the transactions on the blockchain as well as the advanced data analytics techniques, private information can still be inferred by combining the transaction data with various real-world hints [1]. Zcash [8] is the first attempt to use zero-knowledge cryptography to fully encrypt the transactions on the blockchain while such transactions can still be validated. In Hyperledger Fabric, data privacy is achieved by having different channels on the same blockchain platform. Each participant can join different channels, and transaction data in one channel cannot be seen by other channels. In short, how to achieve data privacy is an important consideration before moving to blockchain, and solutions that can share the data in a privacy preserved manner will be helpful.
Hardware fault tolerant
While paying attention to the security of the blockchain software, we should not ignore the fact that the blockchain network is running on multiple normal computers. These computers, especially when running in a less secure environment, can fail due to many reasons, either being hacked by a malicious user or crashing due to software/hardware errors. For example, Ethereum platform users have reported corrupted data files due to false positives of antivirus software, and some Bitcoin users also experienced block checksum mismatch [9]. These users have to re-download all the blockchain transactions in order to recover. This is quite cumbersome and time consuming, especially for a long running blockchain with large amount of data. Therefore, tools are needed to help user effectively validate the integrity of their blockchain nodes, and also quickly recover from the failure.
Regulation compliant
Blockchain also needs to be compliant with the regulations that protect user data privacy. One of the recently activated regulations is GDPR (General Data Protection Regulation) [3]. An important aspect of GDPR is it requires the personal data can be forgotten. In other words, the users have the rights to erase their personal data. Such regulation does provide stronger and more unified personal data protection for Europe Union citizens, but it seems to be contradicted with the design of the blockchain, which guarantees immutable records. Designing regulation-compliant blockchain solutions is becoming appealing but also challenging. One of the solutions is to put the hash of the personal information on the blockchain, while keeping the raw information in an off-chain storage, thus the information can be deleted when necessary. In this case, the hash on the blockchain can be used to validate whether the raw information in off-chain storage is authentic or not. As an alternative, an editable blockchain proposed by Accenture [10] can also be helpful in this case. While preserving the tamper-proof characteristics, such blockchain can be edited by designated authorities, which makes it possible to erase the personal information stored on the chain.
As Vitalik Buterin [13], the co-founder and inventor of Ethereum [14], mentioned: “The main advantage of blockchain technology is supposed to be that it’s more secure, but new technologies are generally hard for people to trust”. Therefore, what we envision is a more secure, privacy-preserving, and regulation-compliant blockchain technology.
References
[1] https://arxiv.org/pdf/1502.01657.pdf
[2] https://arxiv.org/pdf/1805.03490.pdf
[4] https://www.deltadeltaandmoredeltas.com/hash-pointers/
[5] https://en.bitcoin.it/wiki/Proof_of_work
[6] https://ieeexplore.ieee.org/abstract/document/8248566/
[7] https://pdfs.semanticscholar.org/66cc/6e3f36c4282a189249523a5e88577739b736.pdf
[8] https://z.cash/technology/index.html#how-it-works
[9] https://arxiv.org/pdf/1805.01081.pdf
[10] https://link.springer.com/chapter/10.1007/978-3-319-94478-4_18#citeas
[11] https://courses.cs.ut.ee/MTAT.07.022/2017_fall/uploads/Main/janno-report-f17.pdf
[12] https://www.investopedia.com/terms/p/proof-elapsed-time-cryptocurrency.asp
[13] https://en.wikipedia.org/wiki/Vitalik_Buterin
[14] https://www.ethereum.org/
 Qi Zhang received a Ph.D. degree in computer science from Georgia Institute of Technology, Atlanta, USA, in 2017. He is currently a Research Staff Member in IBM Thomas J. Watson Research Center. His research interests include cloud computing, big data processing, distributed systems, and Blockchain systems. He published research articles in referred journals and conference proceedings such as IEEE TC, IEEE TSC, ACM CSUR, VLDB, SC, HPDC, IEEE ICDCS, IEEE ICWS, IEEE CLOUD. Dr. Zhang received the top 5 picks award in IEEE ICWS 2017. He served as a program committee member for IEEE Blockchain 2018. He is also a frequent reviewer for international research journals such as IEEE TSC, IEEE TCC, and international conferences such as ICDCS, SIGMOD, and Middleware.
Qi Zhang received a Ph.D. degree in computer science from Georgia Institute of Technology, Atlanta, USA, in 2017. He is currently a Research Staff Member in IBM Thomas J. Watson Research Center. His research interests include cloud computing, big data processing, distributed systems, and Blockchain systems. He published research articles in referred journals and conference proceedings such as IEEE TC, IEEE TSC, ACM CSUR, VLDB, SC, HPDC, IEEE ICDCS, IEEE ICWS, IEEE CLOUD. Dr. Zhang received the top 5 picks award in IEEE ICWS 2017. He served as a program committee member for IEEE Blockchain 2018. He is also a frequent reviewer for international research journals such as IEEE TSC, IEEE TCC, and international conferences such as ICDCS, SIGMOD, and Middleware.
 Reza M. Parizi is a Software Engineering faculty in the Department of Software Engineering and Game Development at Kennesaw State University, GA, USA. He is a consummate technologist and software engineering researcher with an entrepreneurial spirit at KSU. He is the member of Cyber Scientist- A community of cybersecurity researchers, as well as IEEE, IEEE Blockchain Community, IEEE Computer Society and ACM. Prior to joining KSU, he was an Associate Professor at New York Institute of Technology. He has applied his insights and expertise to a host of innovative and technology driven projects across start-ups, security, software, and education industries. He received a Ph.D. in Software Engineering in 2012 and M.Sc. and B.Sc. degrees in Software Engineering and Computer Science respectively in 2008 and 2005. He has more than 8 years of working experience in industrial software development and project managing. His interests are R&D in Blockchain, smart contract programming, emerging issues in software engineering, and the practice of secure software-run world applications. He has published several research papers in top reputable scientific and international conferences and also has two copyrights to his credit.
Reza M. Parizi is a Software Engineering faculty in the Department of Software Engineering and Game Development at Kennesaw State University, GA, USA. He is a consummate technologist and software engineering researcher with an entrepreneurial spirit at KSU. He is the member of Cyber Scientist- A community of cybersecurity researchers, as well as IEEE, IEEE Blockchain Community, IEEE Computer Society and ACM. Prior to joining KSU, he was an Associate Professor at New York Institute of Technology. He has applied his insights and expertise to a host of innovative and technology driven projects across start-ups, security, software, and education industries. He received a Ph.D. in Software Engineering in 2012 and M.Sc. and B.Sc. degrees in Software Engineering and Computer Science respectively in 2008 and 2005. He has more than 8 years of working experience in industrial software development and project managing. His interests are R&D in Blockchain, smart contract programming, emerging issues in software engineering, and the practice of secure software-run world applications. He has published several research papers in top reputable scientific and international conferences and also has two copyrights to his credit.
 Kim-Kwang Raymond Choo received a Ph.D. in Information Security in 2006 from Queensland University of Technology, Australia. He currently holds the Cloud Technology Endowed Professorship at The University of Texas at San Antonio (UTSA). In 2016, he was named the Cybersecurity Educator of the Year - APAC (Cybersecurity Excellence Awards are produced in cooperation with the Information Security Community on LinkedIn), and in 2015 he and his team won the Digital Forensics Research Challenge organized by Germany's University of Erlangen-Nuremberg. He is the recipient of the 2018 UTSA College of Business Col. Jean Piccione and Lt. Col. Philip Piccione Endowed Research Award for Tenured Faculty, IEEE TrustCom 2018 Best Paper Award, ESORICS 2015 Best Research Paper Award, 2014 Highly Commended Award by the Australia New Zealand Policing Advisory Agency, Fulbright Scholarship in 2009, 2008 Australia Day Achievement Medallion, and British Computer Society's Wilkes Award in 2008. He is also a Fellow of the Australian Computer Society, an IEEE Senior Member, and an Honorary Commander of the 502nd Air Base Wing, Joint Base San Antonio-Fort Sam Houston.
Kim-Kwang Raymond Choo received a Ph.D. in Information Security in 2006 from Queensland University of Technology, Australia. He currently holds the Cloud Technology Endowed Professorship at The University of Texas at San Antonio (UTSA). In 2016, he was named the Cybersecurity Educator of the Year - APAC (Cybersecurity Excellence Awards are produced in cooperation with the Information Security Community on LinkedIn), and in 2015 he and his team won the Digital Forensics Research Challenge organized by Germany's University of Erlangen-Nuremberg. He is the recipient of the 2018 UTSA College of Business Col. Jean Piccione and Lt. Col. Philip Piccione Endowed Research Award for Tenured Faculty, IEEE TrustCom 2018 Best Paper Award, ESORICS 2015 Best Research Paper Award, 2014 Highly Commended Award by the Australia New Zealand Policing Advisory Agency, Fulbright Scholarship in 2009, 2008 Australia Day Achievement Medallion, and British Computer Society's Wilkes Award in 2008. He is also a Fellow of the Australian Computer Society, an IEEE Senior Member, and an Honorary Commander of the 502nd Air Base Wing, Joint Base San Antonio-Fort Sam Houston.
Editor:
 Dr. Shucheng Yu is an Associate Professor of Electrical and Computer Engineering at Stevens Institute of Technology. Before he joined Stevens, Dr. Yu was an associate professor of Computer Science at the University of Arkansas at Little Rock, where he also served as the chair of the Computer Science department and the director of the Computational Research Center of the university. He received his PhD in Electrical and Computer Engineering from Worcester Polytechnic Institute in 2010. His research interest is on cybersecurity in general, with recent focuses on security and privacy for data analytics, security & privacy in smart systems, wireless systems and security. He has published over sixty impactful research articles in academic journals and conference proceedings which have received numerous citations. He has been the editor or guest editor for four international journals, and at the organizing committee for over ten international conferences including IEEE Infocom and IEEE Globecom. He serves the board of trustee for Wireless and Optical Communication Conference (WOCC) and is a member of IEEE and ACM.
Dr. Shucheng Yu is an Associate Professor of Electrical and Computer Engineering at Stevens Institute of Technology. Before he joined Stevens, Dr. Yu was an associate professor of Computer Science at the University of Arkansas at Little Rock, where he also served as the chair of the Computer Science department and the director of the Computational Research Center of the university. He received his PhD in Electrical and Computer Engineering from Worcester Polytechnic Institute in 2010. His research interest is on cybersecurity in general, with recent focuses on security and privacy for data analytics, security & privacy in smart systems, wireless systems and security. He has published over sixty impactful research articles in academic journals and conference proceedings which have received numerous citations. He has been the editor or guest editor for four international journals, and at the organizing committee for over ten international conferences including IEEE Infocom and IEEE Globecom. He serves the board of trustee for Wireless and Optical Communication Conference (WOCC) and is a member of IEEE and ACM.
Subscribe to the IEEE Blockchain Technical Briefs
Join our Blockchain Technical Community and receive our Technical Briefs by email.
IEEE Blockchain Technical Briefs Editorial Board
Gora Datta, FHL7, SMIEEE, SMACM, Managing Editor
2024 Editorial Team
Justin Y. Shi, PhD, Editor-in-Chief
Boleslaw K. Szymanski, PhD
R.L. Shankar, PhD
Imran Bashir
Nicolae "Nicu" Goga, PhD
Constantin “Viorel” Marian, PhD
View the 2023 IEEE Blockchain Technical Briefs Editorial Board
View the 2022 IEEE Blockchain Technical Briefs Editorial Board
View the 2018-2020 IEEE Blockchain Technical Briefs Editorial Board
Past Issues
Read the top five most popular IEEE Blockchain Technical Briefs articles.
Read more (PDF, 731 KB)