Blockchain Facilitated N-Layer Data (Pool) Sharing in the Cloud
Keke Gai, School of Computer Science and Technology, Beijing Institute of Technology, Beijing, China; Kim-Kwang Raymond Choo, Department of Information Systems and Cyber Security and the Department of Electrical and Computer Engineering, University of Texas at San Antonio, San Antonio, TX; and Liehuang Zhu, School of Computer Science and Technology, Beijing Institute of Technology, Beijing, China*
* This work is supported by Beijing Institute of Technology Research Fund Program for Young Scholars (Keke Gai), and the Cloud Technology Endowed Professorship (Kim-Kwang Raymond Choo).
IEEE Blockchain Technical Briefs, June 2019
Discuss this topic on IEEE Collabratec
Abstract
The potential of blockchain for a broad range of applications (e.g., to establish a secure and trustworthy cloud-based data sharing pool) has been explored in recent years, partly due to its unique characteristics, such as tamper resistant, timestamp, and transparency. However, to address commonly raised concerns relating to the sharing of sensitive data, a number of challenges need to be resolved. In this paper, we provide a blockchain-based n-layered approach for enabling sensitive data sharing. One potential use case is the U.S. Department of Homeland Security (DHS)’s Automated Indicator Sharing (AIS) program.
Introduction
Blockchain is, perhaps, commonly associated with Bitcoin. However, blockchain has moved beyond from being Bitcoin or a buzzword to a technology that has been explored and applied in practical applications. For example, in 2017 The University of Melbourne reportedly “its Melbourne Teaching Certificate using the Learning Machine issuing system, an enterprise platform that simplifies anchoring official records to the blockchain”1.
Another application of blockchain is in establishing a traceable and transparent data-driven service system. Such an application differs from Bitcoin as blockchain offers more functionalities beyond financial transactional service [1], [2], [3]. In other words, a blockchain-based system not only provides distributed data storage but also offers other computing services, such as access control, automated control and file protections. This allows users to be able to record critical operations or activities in a chain of blocks over an agreement of consensus, for example in a smart contract-based solution for a business environment. In addition, in blockchain each block’s creation requires a consensus from all relevant stakeholders; hence, allowing us to achieve properties such as tamper-resistant, timestamp, and transparency [2], [4]. Secure data sharing can be enabled because data usage is traceable and access control is facilitated by the consensus-based filter for distinct groups of users. When a request for data access is received, the status of the requester is checked by all stakeholders associated with the data over a consensus, in order to ensure the validity of the request.
Given the data-driven society and increasingly focus on efficient mining of data for a broad range of civilian and government / military settings, the capability to achieve sensitive data sharing securely in an online environment, say in a public-private partnership, will be crucial.
One example where blockchain can play an important role is the Automated Indicator Sharing (AIS) program launched by the U.S. Department of Homeland Security (DHS). The AIS system is designed to facilitate the sharing of cyber threat indicators through a (conventional) secure centralized storage. Such a centralized approach is associated with a single point of failure / attack challenge, how stakeholders can be convinced that privacy is preserved during the data usage cycle, and so on [5]. Such concerns may discourage data owners to participate in such data sharing.
Conceptual Blockchain Facilitated Data (Pool) Sharing Architecture
In this work, we build on our earlier study [6], where we demonstrated that a layered approach based on smart contracts can be used to facilitate secure data sharing, particularly among multiple organizations that have distinct authorizations or operation authorities. Specifically, in the proposed conceptual approach, we classify data users (entities) with diverse authorizations and utilize a blockchain-based solution to govern and trace data. Super nodes with higher-level voting weights are introduced in this approach so that malicious voting-related attacks can be effectively mitigated, especially in the context of the permissioned blockchain. The operation of the authorization is supported by the underpinning smart contract(s), in which authorizations are assigned in terms of user identities. Data user in our approach is defined to be a party who intends to access data, either an individual user or an organization/enterprise. What’s more, using blockchain-based data pool also can enhance the willingness of data sharing, since rewards can be offered on the chain to motivate such sharing. We remark that the rewards need not be financial in nature. For example, in the context of the AIS program, rewards can be membership tier where active contributors may have access or priority to certain resources (e.g., in-depth analysis of shared data at a reduced rate or complimentary, or earlier access to certain cyber threat information).
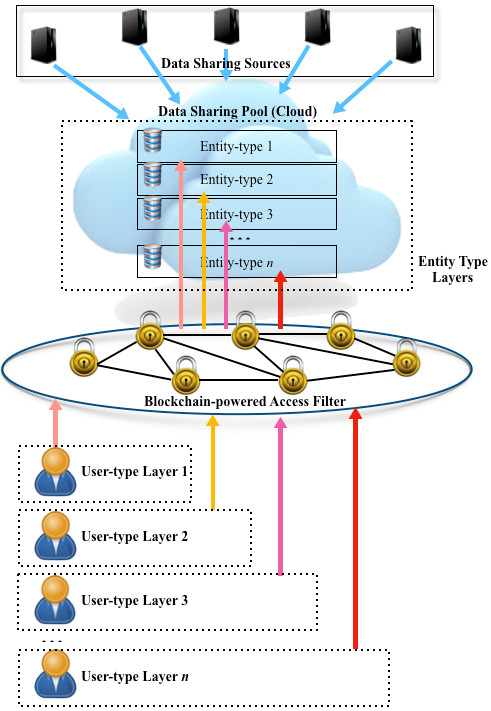
The proposed approach is an information-centric architecture, where achieving an effective data access filter for various user groups is our primary design goal. The content stored in the data pool needs to be grouped into layers, based on the level of data sensitivity. The key value of blockchain-based multi-layer data sharing is to facilitate a fine-grained access control that relies on the consensus, as well as traceable validations. The proposed multi-layer approach can be applied in scenarios when a complex user group setting is required to define access authorizations. There are, however, a number of considerations in the context of multi-access, such as infrastructure mapping or unauthorized data usage, due to lack of data life cycle supervision. Integrating data usage agreement with data provenance is an alternative solution, which can be achieved by implementing a blockchain-based layered access filter. For example, the latter can be based on cyber threat level (e.g., urgent / time-sensitive), privacy protection level, or classification level (e.g., Confidential, Secret, or Top Secret). In the context of the AIS program, to locate certain cyber threat risk(s), data in the pool depict vulnerabilities and cyber threats and not all private sector participants (data users) are authorized to access all data in the pool. For example, a data user with authority to access Secret-level information will not be able to access data classified at the Top Secret level. For authentication, we can either use existing mechanism or those proposed in the literature [7], [8]. Fig. 1 below presents the architecture of the proposed model.
Figure 1. Architecture of the proposed n-layer approach.
We will now briefly describe the operation procedure and key components of the conceptual architecture.
The first step is to establish an automated control mechanism on a blockchain system, which groups data packages and filters data users. This can be achieved using existing smart contracts. For example, we can use smart contract to label the input data package when data are contributed (shared in the pool). The label can be created by reading attributes of the data package (e.g. from the header or other metadata) and follow the priority setting of the system, such as preserving privacy or classification level. The label is broadcasted so that a new record (block) will be created on the ledger if a consensus can be made. Data users wanting to access the data do so by sending a request to the smart contract. Each data user also has a level label that is achieved over a consensus agreement on the blockchain; hence, smart contract can easily determine the authorization by reading the users’ labels. After the request is approved or denied, a new block will be created to record the action. This can be used to facilitate future audit or forensic investigation. A label mapping mechanism is the fundamental of interconnecting the authorization and information-access.
In addition to the labels, we can also restrict access to information based on the entity type. For example, in this second layer, each entity (data user) is assigned an entity-type label, such as entity-type 1, entity-type 2, entity-type 3, etc. For example, entity-type 1 may refer to typical private sector entities, entity-type 2 may refer to private sector entities that are also U.S. Government “trusted” contractors, entity-type 3 are for general U.S. Government entities, entity-type 4 for U.S. law enforcement community, entity-type 5 for U.S. defense community, entity-type 6 for U.S. intelligence community, and so on.
Additional layers can be introduced, based on the requirements of the applications. Moreover, according to the objective of the data pool establishment (e.g. preserving privacy [9]), data package is labeled using the same standard of the level configuration. Thus, a mapping between information and user entities can be built. Once the request is approved, data users will be authorized to download/access the data from the approved portion of the data pool.
Our study also notices that a layered blockchain approach can be leveraged in not only sensitive data sharing but also numerous other operations, such as secure multi-part interactions, governable data synchronizations, or trustfulness evaluations and forensics. A few research directions will guide our future work.
Limitations and Future Work
There are, however, challenges in such a layered blockchain system. For example, an adversarial node (e.g., a compromised or corrupted data user) in the blockchain system with even the lowest authorization level can seek to impersonate a fully authorized node, once it acquires sufficient access information from other legitimate nodes in the system. Such an attack scenario is applicable to many other conventional network-related scenarios [10], such as infrastructure mapping attacks or middleman-attacks.
Identity-authorization mapping in blockchain is also challenging when the system becomes public and adversaries can legitimately join the network. Another potential research direction is to design a highly efficient consensus mechanism for layered blockchain system. This is currently a challenging topic, as one has to fully consider achieving both consensus efficiency and secure implementation. If we focus on performance (i.e., efficiency) over security, then there is a higher risk of malfunction in the blockchain due to its tamper-resistant characteristic [11]. Hence, we need to determine an optimal trade-off level between performance and security, based on the specific application requirements.
There are a number of potential future extensions, and we will now describe three such future research focuses. First, there is a need to evaluate the proposed approach in a broader range of real-world applications and diverse contexts, with the aims of identifying additional features/functionalities that need to be supported within the framework. Second, we will explore other novel access control schemes in blockchain, such as those that use hidden validation methods in order to minimize the limitations associated with the open-nature of blockchain. In addition, based on our prior study [12], we will also investigate the requirements of privacy-preserving mechanisms in blockchain systems, when multiple user groups are involved. For example, how do we ensure that information stored in the blocks (and are publicly available) can be protected from attacks such as data mining attacks and linkage attacks?
1http://newsroom.melbourne.edu/news/university-melbourne-issue-recipient-owned-blockchain-records (last accessed, 26th November 2018)
References
[1] K. Gai, K.-K.R. Choo, and L. Zhu. Blockchain-Enabled Reengineering of Cloud Datacenters. IEEE Cloud Computing, 5(6), 21-25, 2018.
[2] M. Banerjee, J. Lee, and K.-K.R. Choo. A blockchain future for Internet of Things security: a position paper. Digital Communications and Networks, 4(3):149–160, 2018.
[3] J. Kang, R. Yu, X. Huang, S. Maharjan, Y. Zhang, and E. Hossain. Enabling localized peer-to-peer electricity trading among plug-in hybrid electric vehicles using consortium blockchains. IEEE Transactions on Industrial Informatics, 13(6):3154–3164, 2017.
[4] Z. Li, J. Kang, R. Yu, D. Ye, Q. Deng, and Y. Zhang. Consortium blockchain for secure energy trading in industrial Internet of Things. IEEE Transactions on Industrial Informatics, 14(8):3690–3700, 2018.
[5] Z. Zhang, W. Cao, Z. Qin, L. Zhu, Z. Yu, and K. Ren. When privacy meets economics: Enabling differentially-private battery supported meter reporting in smart grid. In Quality of Service (IWQoS), 2017 IEEE/ACM 25th International Symposium on pages 1–9, Vilanova i la Geltru, Spain, 2017. IEEE.
[6] L. Zhu, Y. Wu, K. Gai, and K.K.R. Choo. Controllable and trustworthy blockchain-based cloud data management. Future Generation Computer Systems, 91:527–535, 2019.
[7] C. Lin, D. He, X. Huang, K.K.R. Choo, and A.V. Vasilakos. BSeIn: A blockchain-based secure mutual authentication with fine-grained access control system for industry 4.0. Journal of Network and Computer Applications, 116: 42-52, 2018.
[8] Y. Zhang, D. He, and K.K.R. Choo. BaDS: Blockchain-Based Architecture for Data Sharing with ABS and CP-ABE in IoT. Wireless Communications and Mobile Computing, 2018: Article ID 2783658 (9 pages), 2018.
[9] Z. Zhang, Z. Qin, L. Zhu, J. Weng, and K. Ren. Cost-friendly differential privacy for smart meters: Exploiting the dual roles of the noise. IEEE Trans. Smart Grid, 8(2):619–626, 2017.
[10] Y. Zhang, R. Yu, S. Xie, W. Yao, Y. Xiao, and M. Guizani. Home M2M networks: architectures, standards, and QoS improvement. IEEE Communications Magazine, 49(4):44–52, 2011.
[11] K. Gai, Y. Wu, L. Zhu, L. Xu, and Y. Zhang. Permissioned Blockchain and Edge Computing Empowered Privacy-preserving Smart Grid Networks, IEEE Internet of Things Journal, PP(99), 1-14, 2019.
[12] K. Gai, Y. Wu, L. Zhu, M. Qiu, and M. Shen. Privacy-preserving Energy Trading Using Consortium Blockchain in Smart Grid. IEEE Transactions on Industrial Informatics, PP(99), 1-11, 2019.
 Keke Gai holds degrees from Nanjing University of Science and Technology (BEng), the University of British Columbia (MET) and Lawrence Technological University (MBA and MS). He is currently pursuing his PhD at the Department of Computer Science at Pace University, New York. Keke Gai has published more than 90 peer-reviewed journal or conference papers, more than 30 journal papers (including ACM/IEEE Transactions), and more than 50 conference papers. He has been granted three IEEE Best Paper Awards (IEEE TrustCom’ 18, IEEE HPCC’ 18, IEEE SSC '16, IEEE CSCloud '15, IEEE BigDataSecurity '15) and two IEEE Best Student Paper Awards (IEEE HPCC '16, IEEE SmartCloud '16) by IEEE conferences in recent years. His paper about cloud computing has been granted the Most Downloaded Articles of Journal of Network and Computer Applications (JNCA) in 2016. He is involved in a number of professional/academic associations, including ACM and IEEE. Currently, he is serving as the Secretary/Treasurer of the IEEE STC (Special Technical Community) in Smart Computing at the IEEE Computer Society. He has worked for a few Fortune 500 enterprises, including SINOPEC and GE Capital. His research interests include cyber security, edge computing, blockchain, and cloud computing.
Keke Gai holds degrees from Nanjing University of Science and Technology (BEng), the University of British Columbia (MET) and Lawrence Technological University (MBA and MS). He is currently pursuing his PhD at the Department of Computer Science at Pace University, New York. Keke Gai has published more than 90 peer-reviewed journal or conference papers, more than 30 journal papers (including ACM/IEEE Transactions), and more than 50 conference papers. He has been granted three IEEE Best Paper Awards (IEEE TrustCom’ 18, IEEE HPCC’ 18, IEEE SSC '16, IEEE CSCloud '15, IEEE BigDataSecurity '15) and two IEEE Best Student Paper Awards (IEEE HPCC '16, IEEE SmartCloud '16) by IEEE conferences in recent years. His paper about cloud computing has been granted the Most Downloaded Articles of Journal of Network and Computer Applications (JNCA) in 2016. He is involved in a number of professional/academic associations, including ACM and IEEE. Currently, he is serving as the Secretary/Treasurer of the IEEE STC (Special Technical Community) in Smart Computing at the IEEE Computer Society. He has worked for a few Fortune 500 enterprises, including SINOPEC and GE Capital. His research interests include cyber security, edge computing, blockchain, and cloud computing.
 Kim-Kwang Raymond Choo received a Ph.D. in Information Security in 2006 from Queensland University of Technology, Australia. He currently holds the Cloud Technology Endowed Professorship at The University of Texas at San Antonio (UTSA). In 2016, he was named the Cybersecurity Educator of the Year - APAC (Cybersecurity Excellence Awards are produced in cooperation with the Information Security Community on LinkedIn), and in 2015 he and his team won the Digital Forensics Research Challenge organized by Germany's University of Erlangen-Nuremberg. He is the recipient of the 2018 UTSA College of Business Col. Jean Piccione and Lt. Col. Philip Piccione Endowed Research Award for Tenured Faculty, Outstanding Associate Editor of 2018 for IEEE Access, IEEE TrustCom 2018 Best Paper Award, ESORICS 2015 Best Research Paper Award, 2014 Highly Commended Award by the Australia New Zealand Policing Advisory Agency, Fulbright Scholarship in 2009, 2008 Australia Day Achievement Medallion, and British Computer Society's Wilkes Award in 2008. He is also a Fellow of the Australian Computer Society, an IEEE Senior Member, and Co-Chair of IEEE Multimedia Communications Technical Committee (MMTC)’s Digital Rights Management for Multimedia Interest Group.
Kim-Kwang Raymond Choo received a Ph.D. in Information Security in 2006 from Queensland University of Technology, Australia. He currently holds the Cloud Technology Endowed Professorship at The University of Texas at San Antonio (UTSA). In 2016, he was named the Cybersecurity Educator of the Year - APAC (Cybersecurity Excellence Awards are produced in cooperation with the Information Security Community on LinkedIn), and in 2015 he and his team won the Digital Forensics Research Challenge organized by Germany's University of Erlangen-Nuremberg. He is the recipient of the 2018 UTSA College of Business Col. Jean Piccione and Lt. Col. Philip Piccione Endowed Research Award for Tenured Faculty, Outstanding Associate Editor of 2018 for IEEE Access, IEEE TrustCom 2018 Best Paper Award, ESORICS 2015 Best Research Paper Award, 2014 Highly Commended Award by the Australia New Zealand Policing Advisory Agency, Fulbright Scholarship in 2009, 2008 Australia Day Achievement Medallion, and British Computer Society's Wilkes Award in 2008. He is also a Fellow of the Australian Computer Society, an IEEE Senior Member, and Co-Chair of IEEE Multimedia Communications Technical Committee (MMTC)’s Digital Rights Management for Multimedia Interest Group.
 Liehuang Zhu received his Ph.D. degree in computer science from Beijing Institute of Technology, Beijing, China, in 2004. he is currently a professor at School of Computer Science & Technology, Beijing Institute of Technology. Professor Zhu has published more than 180 peer-reviewed SCI/EI papers and has been granted a few IEEE Best Paper Awards, including IWQoS 2018, TrustCom 2018, and IPCCC 2014. His research interests include security protocol analysis and design, wireless sensor networks, and cloud computing.
Liehuang Zhu received his Ph.D. degree in computer science from Beijing Institute of Technology, Beijing, China, in 2004. he is currently a professor at School of Computer Science & Technology, Beijing Institute of Technology. Professor Zhu has published more than 180 peer-reviewed SCI/EI papers and has been granted a few IEEE Best Paper Awards, including IWQoS 2018, TrustCom 2018, and IPCCC 2014. His research interests include security protocol analysis and design, wireless sensor networks, and cloud computing.
Editor:
 Yan Zhang is Full Professor at the Department of Informatics, University of Oslo, Norway. He received a PhD degree in School of Electrical & Electronics Engineering, Nanyang Technological University, Singapore. He is an Associate Technical Editor of IEEE Communications Magazine, an Editor of IEEE Network Magazine, an Editor of IEEE Transactions on Green Communications and Networking, an Editor of IEEE Communications Surveys & Tutorials, an Editor of IEEE Internet of Things Journal, an Editor of IEEE Vehicular Technology Magazine, and an Associate Editor of IEEE Access. He serves as chair positions in a number of conferences, including IEEE GLOBECOM 2017, IEEE VTC-Spring 2017, IEEE PIMRC 2016, IEEE CloudCom 2016, IEEE ICCC 2016, IEEE CCNC 2016, IEEE SmartGridComm 2015, and IEEE CloudCom 2015. He serves as TPC member for numerous international conference including IEEE INFOCOM, IEEE ICC, IEEE GLOBECOM, and IEEE WCNC. His current research interests include: next-generation wireless networks leading to 5G, green and secure cyber-physical systems (e.g., smart grid, healthcare, and transport). He is IEEE VTS (Vehicular Technology Society) Distinguished Lecturer. He is also a senior member of IEEE, IEEE ComSoc, IEEE CS, IEEE PES, and IEEE VT society.
Yan Zhang is Full Professor at the Department of Informatics, University of Oslo, Norway. He received a PhD degree in School of Electrical & Electronics Engineering, Nanyang Technological University, Singapore. He is an Associate Technical Editor of IEEE Communications Magazine, an Editor of IEEE Network Magazine, an Editor of IEEE Transactions on Green Communications and Networking, an Editor of IEEE Communications Surveys & Tutorials, an Editor of IEEE Internet of Things Journal, an Editor of IEEE Vehicular Technology Magazine, and an Associate Editor of IEEE Access. He serves as chair positions in a number of conferences, including IEEE GLOBECOM 2017, IEEE VTC-Spring 2017, IEEE PIMRC 2016, IEEE CloudCom 2016, IEEE ICCC 2016, IEEE CCNC 2016, IEEE SmartGridComm 2015, and IEEE CloudCom 2015. He serves as TPC member for numerous international conference including IEEE INFOCOM, IEEE ICC, IEEE GLOBECOM, and IEEE WCNC. His current research interests include: next-generation wireless networks leading to 5G, green and secure cyber-physical systems (e.g., smart grid, healthcare, and transport). He is IEEE VTS (Vehicular Technology Society) Distinguished Lecturer. He is also a senior member of IEEE, IEEE ComSoc, IEEE CS, IEEE PES, and IEEE VT society.
Subscribe to the IEEE Blockchain Technical Briefs
Join our Blockchain Technical Community and receive our Technical Briefs by email.
IEEE Blockchain Technical Briefs Editorial Board
Gora Datta, FHL7, SMIEEE, SMACM, Managing Editor
2024 Editorial Team
Justin Y. Shi, PhD, Editor-in-Chief
Boleslaw K. Szymanski, PhD
R.L. Shankar, PhD
Imran Bashir
Nicolae "Nicu" Goga, PhD
Constantin “Viorel” Marian, PhD
View the 2023 IEEE Blockchain Technical Briefs Editorial Board
View the 2022 IEEE Blockchain Technical Briefs Editorial Board
View the 2018-2020 IEEE Blockchain Technical Briefs Editorial Board
Past Issues
Read the top five most popular IEEE Blockchain Technical Briefs articles.
Read more (PDF, 731 KB)