Blockchain Value Realization
Promises, Realities, and the Journey towards Integration and Adoption
Hazim Dahir; and Ammar Rayes, Cisco Systems
IEEE Blockchain Technical Briefs, September 2019
Discuss this topic on IEEE Collabratec
Blockchain is not ready for prime time. You can stop reading now. However, since most people observing the momentum behind blockchain would disagree, you probably should keep reading. There is no doubt the momentum and investments are increasing, however, the integration of Blockchain into a workflow or process is where the issue is. Furthermore, there is high level of certainty that blockchain will revolutionize how we conduct business (all business).
Companies, supply chains, operations, or logistics are run or governed by a group of interlinked business applications that rely on the existence of various types and sources of “data”. There is a strong sense that Blockchain is too much of a disruption to the existing business model to be taken lightly by decision makers. They feel that they need to re-invent the business model and all its elements (including their people and their skill levels).
Through our work, we interact with a group of clients representing multiple verticals (Financials, Manufacturing, Transportation, etc.). Those clients are looking at IoT-type solutions for improving the efficiency and productivity of their business through data acquisition and manipulation and higher visibility of operations. Data used to make important decisions must be trustworthy and the trustworthiness of the data requires both security and integrity measures, among other things. Blockchain can help or in some cases may be the answer.
Depending on the use-case and application, the majority of IoT scenarios are expected to experience massive amount of data generated and transported by a massive number of devices. In the area of data security, practitioners focus on ensuring Confidentiality, Integrity, and Availability. Integrity usually means: no unauthorized modification of data regardless of how far or near it is from its source. And that’s exactly where blockchain closes a huge gap for IoT. In addition, the distributed nature of blockchain ensures that no single point of failure affects the integrity of the data or the process from which it was generated.
When we “unofficially” survey our customers we can easily categorize them into one of the following areas:
- A group of clients that use the phrases “it’s a Hype” and will need more years to become real.
- A group that describe themselves as being in the “Investigation” phase.
- A group that describe themselves as “when it comes to Blockchain, we need to see demonstrable successes before we attempt (followers not leaders).
- And, yes, as expected, a small group of early adopters running one or several proof-of-concepts and possibly limited deployments but with little consideration of the integration or adoption big picture.
Blockchain is not a “technology” to be deployed in the traditional sense of software and hardware, but rather a group of technologies and services that enable the digitization of various processes across the boundaries of multiple enterprises. It can cross silo boundaries without necessarily requiring a large investment in making them all compatible. And this is why, careful considerations of the use cases and the eco-systems of applications and processes that represent them is highly recommended.
In the following few paragraphs, we will illustrate the key benefits Blockchain and the challenges of deploying it by considering an Internet of Things (IoT) example.
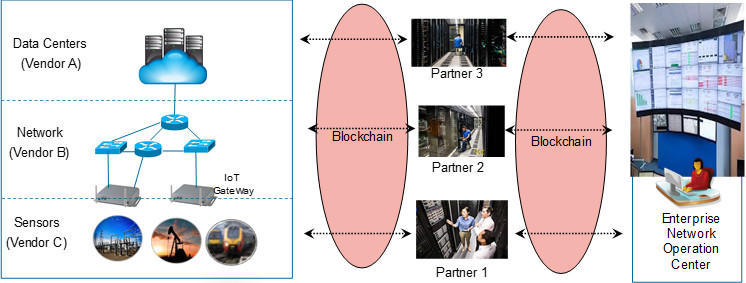
Figure 1. Typical IoT Management Example
A typical IoT network may be divided into three main layers:
- Sensing layer (sensors, actuators and IoT getaways),
- Transport layer (routing and switching), and
- Cloud layer (Data Centers) as shown in Figure 1.
Almost certainly, systems (hardware and software applications) for these layers are manufactured by different vendors (i.e. Vendor A, B and C as shown the above Figure)1. These layers are also deployed and managed by different partners (e.g. partner 1 manages the health of sensors and actuators, partner 2 manages the health of routing and switching and partner 3 manages the health and performance of the data center devices and services).
The depth of contracts among the vendors, partners and the Enterprise or Service Provider (i.e. network owner) vary between companies and typically depend on the structure, resources and expertise of the enterprise or service provider. It can range from a limited device warranty service where vendors are responsible for the health of their devices by providing support services, ranging from call-center support and RMA (Return Material Authorization) to full Managed Service where the network vendor and/or its partner is responsible for the comprehensive management functions as well as the end-to-end services offered by the network owner to end customers. In this case, the enterprise / service provider may own some aspect of the service management (e.g. in charge of monitoring and fixing level 0 and level 1 problems). A partner owns more complex aspects of service management (e.g. level 2) and the vendor is responsible for levels 3 and 4 which may include fixing defects by subject matter experts as w ell as, RMAs and firmware update support.
As illustrated in Figure 1, data sharing (e.g. sensors sending health alerts to a partner and vendor) is essential for successful services IoT networks. At the same time, data privacy and security is becoming even more important. Violations of user privacy and digital rights management in form of unintended data use, corporate applications and security breaches are being widely reported across multiple sources [2].
Blockchain distributed ledger technology (DLT) with the ability to bridge the gap between trustless parties and synchronize digital data geographically spread across multiple sites and parties and without needing a central administrator or centralized data storage as in previous technologies. It maintains a common consensus view among groups of distributed but nodes without expensive central controllers. We recommend use it to create a distributed trust between vendors, partners, service providers as well as end customers by providing various contract levels. Participants in the network may be entities or organizations that provide resources or support an enterprise or service provide through a permissioned consortium network.”
1 Example: The network vendor may be Cisco. Partners for network services may be. IBM, Accenture or ServiceNow). Enterprise or Service Provider may be Walmart or AT&T (providing IoT-based services for hospitals)
References:
- A. Rayes and S. Salam, “IoT Form Hype to Reality,” Springer 2018: https://www.springer.com/gp/book/9783319995151
- “Revealed: 50 million Facebook profiles harvested for Cambridge Analytica in major data breach,” July 13, 2019, http://www.mr-mehra.com/2018/03/revealed-50-million-facebook-profiles.html
- P.-H. Kuo, A. Mourad, and J. Ahn, ‘‘Potential applicability of distributed ledger to wireless networking technologies,’’ IEEE Wireless Communications., vol. 25, no. 4, pp. 4–6, Aug. 2018.
 Dr. Ammar Rayes [S’85, M’91, SM’15] is a Distinguished Engineer at Cisco customer Experience’s CTO Office working on the Technology Strategy. His research interests include Network and Applications Analytics, IoT and AI/ML.
Dr. Ammar Rayes [S’85, M’91, SM’15] is a Distinguished Engineer at Cisco customer Experience’s CTO Office working on the Technology Strategy. His research interests include Network and Applications Analytics, IoT and AI/ML.
He has authored over 100 publications in refereed journals and conferences on advances in software & networking related technologies, 4 Books and over 30 US and International patents. He is the Founding President and board member of the International Society of Service Innovation Professionals www.issip.org, Adjunct Professor at San Jose State University, Editor-in-Chief of Advances of Internet of Things Journal, Editorial Board Member of IEEE Blockchain News Brief, Transactions on Industrial Networks and Intelligent Systems, Journal of Electronic Research and Application and the European Alliance for Innovation - Industrial Networks and Intelligent Systems. He has served as Associate Editor of ACM Transactions on Internet Technology and Wireless Communications and Mobile Computing Journals, Guest Editor of multiple journals and over half a dozen IEEE Communication or Network Magazine issues, co-chaired the Frontiers in Service Conference and appeared as Keynote speaker at several IEEE and industry Conferences: https://sites.google.com/view/ammarrayes/home
He received his BS and MS Degrees in EE from the University of Illinois at Urbana and his Ph.D. degree in EE from Washington University in St. Louis, Missouri, where he received the Outstanding Graduate Student Award in Telecommunications.
 Hazim Dahir is a distinguished engineer at the Cisco Customer Experience office of the CTO. He is working to define or influence next generation Digital Transformation Architectures across multiple technologies and verticals. Hazim is currently focusing on developing Cybersecurity and Data Analytics solutions for multiple IoT verticals and use-cases.
Hazim Dahir is a distinguished engineer at the Cisco Customer Experience office of the CTO. He is working to define or influence next generation Digital Transformation Architectures across multiple technologies and verticals. Hazim is currently focusing on developing Cybersecurity and Data Analytics solutions for multiple IoT verticals and use-cases.
He is a contributing member of workgroups within the Industrial Internet Consortium (IIC) and IEEE on Edge and Fog technologies. He has multiple issued and pending patent filings with the USPTO and is a frequent presenter at US and International Conferences. Hazim is the author and co-author of a book on IOT strategies as well as several whitepapers on design best practices guidelines.
He received his BSEE and MSc from North Carolina State University. He also holds continuing education certificates in Data Science and Cybersecurity from NC State and MIT.
Editor:
 Andy Lippman is a Senior Scientist at MIT and founding associate director of the MIT Media Lab. He got his BS and MS at MIT, and PhD at EPFL, Lausanne. He has worked for 45 years on personal computing, networking and interactive systems. In the 1980s he directed the “Movie-Map” project that presaged Google's streetview. He helped pioneer visual computing and communications systems such as MPEG and digital HDTV. His current research group addresses Viral Communications, systems that are often peer-to-peer and can grow organically through adoption rather than a priori agreement. He has studied blockchains and digital currency for six years. Some recent work involves developing personal networks for social action and a blockchain-based identity control system for medical records.
Andy Lippman is a Senior Scientist at MIT and founding associate director of the MIT Media Lab. He got his BS and MS at MIT, and PhD at EPFL, Lausanne. He has worked for 45 years on personal computing, networking and interactive systems. In the 1980s he directed the “Movie-Map” project that presaged Google's streetview. He helped pioneer visual computing and communications systems such as MPEG and digital HDTV. His current research group addresses Viral Communications, systems that are often peer-to-peer and can grow organically through adoption rather than a priori agreement. He has studied blockchains and digital currency for six years. Some recent work involves developing personal networks for social action and a blockchain-based identity control system for medical records.
Subscribe to the IEEE Blockchain Technical Briefs
Join our Blockchain Technical Community and receive our Technical Briefs by email.
IEEE Blockchain Technical Briefs Editorial Board
Gora Datta, FHL7, SMIEEE, SMACM, Managing Editor
2024 Editorial Team
Justin Y. Shi, PhD, Editor-in-Chief
Boleslaw K. Szymanski, PhD
R.L. Shankar, PhD
Imran Bashir
Nicolae "Nicu" Goga, PhD
Constantin “Viorel” Marian, PhD
View the 2023 IEEE Blockchain Technical Briefs Editorial Board
View the 2022 IEEE Blockchain Technical Briefs Editorial Board
View the 2018-2020 IEEE Blockchain Technical Briefs Editorial Board
Past Issues
Read the top five most popular IEEE Blockchain Technical Briefs articles.
Read more (PDF, 731 KB)